Trezor Login – A Simple Guide to Secure Crypto Access
Managing cryptocurrency safely starts with choosing the right hardware wallet, and Trezor remains one of the most trusted options. The Trezor login process is designed to give users a secure, seamless way to access their digital assets without compromising privacy or funds. Whether you’re a beginner or an experienced trader, understanding the login steps can help you stay protected while navigating the crypto world.
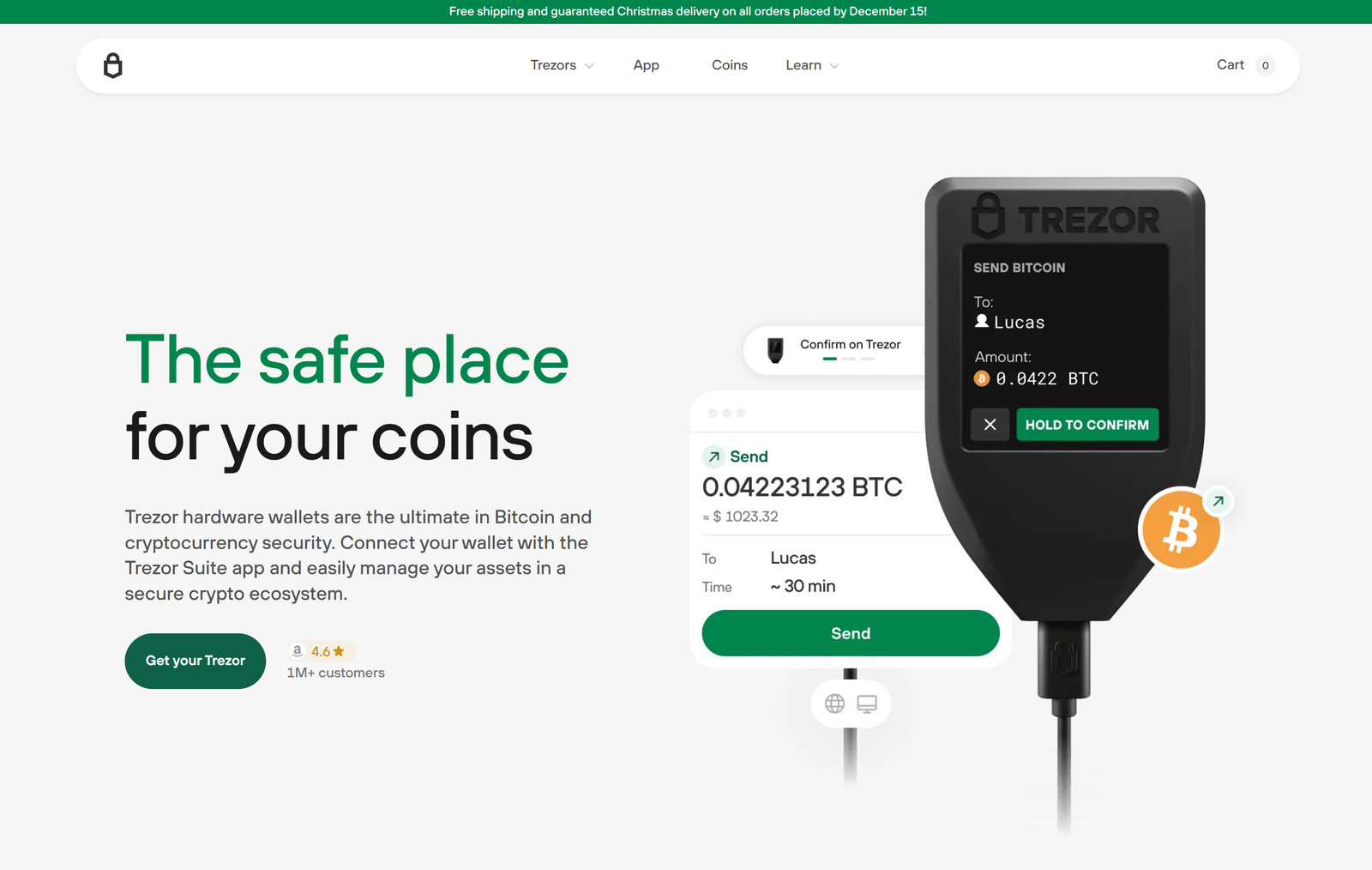
To begin, simply connect your Trezor device to your computer using a USB cable and visit the official Trezor website or Trezor Suite application. From there, select your device model and follow the prompts to continue. One of the standout features of Trezor login is that it never exposes your private keys. All sensitive information stays inside the device, giving you full control and an extra layer of protection against online threats.
You’ll be required to enter your PIN on the device itself, ensuring no one can access your wallet without physical possession. For added security, users can also enable passphrases, which act as a second password. This feature gives you an invisible vault inside your wallet, making unauthorized access nearly impossible.
Trezor also offers a clean and intuitive interface that allows users to check balances, manage crypto, track portfolio performance, and even initiate transactions with ease. Every login session is fully encrypted, and the device includes built-in recovery methods in case it's lost or damaged.
Advantages of Using Trezor Login
Enhanced Security: Private keys never touch the internet.
User-Friendly Interface: Easy navigation for beginners and pros.
PIN & Passphrase Protection: Multi-layered defense against intruders.
Compatibility: Works with major coins and third-party wallets.
Offline Safety: Hardware-based protection keeps assets secure.
With strong security features and a smooth login experience, Trezor helps users manage digital assets confidently and safely.